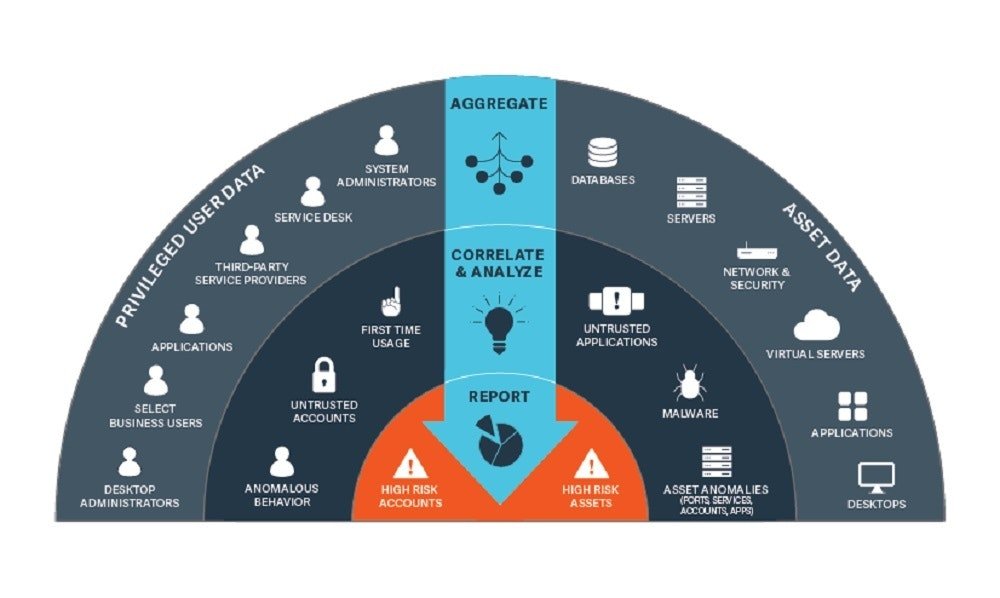
Privileged Access Management (PAM) is a vital security strategy for protecting accounts that hold elevated permissions and access to critical information systems. These accounts, often used by system administrators or other high-level users, control essential system changes and manage sensitive data. Because of their wide-reaching access, privileged accounts are highly attractive targets for both cybercriminals and malicious insiders.
By implementing PAM, organizations can control, monitor, and secure privileged account activity, significantly reducing the risk of unauthorized access. PAM also plays an essential role in enforcing security policies, preventing data breaches, and ensuring compliance with industry regulations. In short, a well-managed PAM program is a cornerstone of any strong cybersecurity framework.
Why Privileged Access Management (PAM) Matters
PAM provides several key benefits that strengthen the security of sensitive accounts and data:
Mitigating Insider Threats
Employees, contractors, and third parties with elevated access can pose risks—either through negligence or intentional misuse. PAM enforces strict permission controls and continuous monitoring, ensuring that only authorized personnel can access critical systems.
Ensuring Regulatory Compliance
Industries such as healthcare, finance, and energy operate under strict regulations like GDPR, HIPAA, and PCI DSS, which demand controlled and auditable access to sensitive data. PAM enforces the principle of least privilege—granting users access only to the information they need for their roles—and maintains detailed logs to prove compliance during audits.
Protecting Administrative Privileges
Administrative accounts are prime targets for attackers. Without PAM, poor authorization practices can leave these accounts exposed. PAM solutions limit access to specific job functions, enforce time-bound privileges, and require multi-factor authentication (MFA), providing additional layers of security.
Preventing Widespread Breaches
If an account is compromised, PAM’s restrictions limit the intruder’s ability to move freely within the network, reducing the potential for large-scale breaches. Continuous monitoring also allows organizations to detect suspicious behavior and respond quickly to threats.
Challenges in Implementing PAM
While PAM is essential, it comes with its own set of complexities:
Account Sprawl
Privileged accounts often exist across multiple systems and applications, making them difficult to track and secure—especially in organizations with high staff turnover.
Maintaining Least Privilege
Assigning just the right level of access is challenging in dynamic work environments where job roles change frequently.
Monitoring and Auditing
Tracking every privileged action generates large volumes of data, which can overwhelm security teams if alerts are not properly configured.
System Integration
PAM must work seamlessly with existing identity management systems, firewalls, and other security infrastructure, which can require significant effort and expertise.
Ongoing Policy Management
Access policies must evolve alongside the organization. Neglecting regular reviews can lead to outdated controls and potential vulnerabilities.
Expert Support for Effective PAM
Deploying PAM effectively often requires specialized expertise. Security professionals help organizations:
Conduct risk assessments to identify high-risk accounts and critical systems.
Develop custom access control policies based on least privilege and MFA enforcement.
Implement real-time monitoring and alerts to detect suspicious activities.
Perform regular audits to ensure compliance and identify weaknesses.
Provide staff training to ensure everyone understands PAM best practices.
Deliver incident response support to contain and resolve security breaches quickly.
Organizations that work with PAM experts are better equipped to reduce vulnerabilities, maintain compliance, and protect their most valuable assets.
Conclusion
Privileged Access Management is essential for safeguarding high-risk accounts and critical systems from unauthorized access. By enforcing strict access controls, continuously monitoring account activity, and integrating PAM with existing security infrastructure, organizations can significantly reduce insider threats, comply with regulations, and strengthen their cybersecurity posture.
For a tailored PAM solution that protects your business operations, contact our team today. We provide the expertise, tools, and support you need to keep your critical systems secure.